Recently, I stumbled upon a very annoying WordPress Site Health error related to Jetpack. Despite trying multiple solutions like reinstalling the plugin, reconfiguring, and reconnecting, I consistently faced the same critical connection issue. Frustrated, I delved deeper for solutions, but found nothing relevant for a long time… until I did.
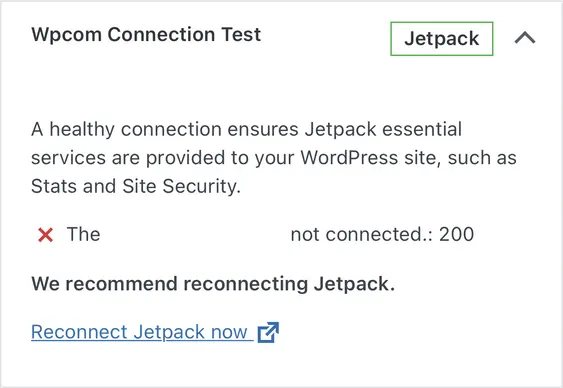
Jetpack offers a couple of solutions on their website, but none of them worked for me. As it turned out, in my case there was a default configuration file added by DigitalOcean which redirected a specific php file to the homepage.
If you’re using a default DigitalOcean WordPress droplet from DigitalOcean Marketplace and encounter a Jetpack reconnection error, the issue might be due to the default security settings redirecting the xmlrpc.php file.
Here’s how I managed to fix it.
Understanding the problem
DigitalOcean’s WordPress droplet includes a configuration that redirects xmlrpc.php to enhance security. This can block Jetpack, which relies on xmlrpc.php.
Purpose of block-xmlrpc.conf
The file block-xmlrpc.conf was likely added as part of a security measure when you installed WordPress. The purpose of this configuration is to block access to the xmlrpc.php file by redirecting any requests for it to the root directory.
Purpose of xmlrpc.php
The xmlrpc.php file in WordPress enables remote connections, allowing external applications to interact with WordPress, such as publishing posts remotely or managing comments. However, it has been a target for various types of attacks, including brute force and DDoS attacks.
Why block xmlrpc.php?
- Security: Blocking access to
xmlrpc.phphelps mitigate potential security vulnerabilities. - Reduce Attack Surface: Reducing endpoints that can be targeted by attackers.
- Performance: Preventing unnecessary requests to
xmlrpc.phpcan improve site performance.
Alternative approaches:
- Restrict Access by IP: Only allow specific IP addresses to access
xmlrpc.php. - Use a Security Plugin: Many WordPress security plugins provide options to secure or block
xmlrpc.phpwithout completely disabling its functionality.

Solution: Find and update the configuration file
- Check for additional Apache configuration files.
- Identify and edit the configuration file.
- Allow Jetpack IPs while blocking others.
- Enable the configuration and restart Apache.
- Verify and test your new configuration.
Step 1: Check for additional Apache configuration files
Sometimes, other Apache configuration files might affect the behavior. Check the /etc/apache2/conf-available and /etc/apache2/conf-enabled directories for any additional configurations.
ls /etc/apache2/conf-available/
ls /etc/apache2/conf-enabled/Look for any configurations that might affect redirects or rewrite rules. For instance, you might find block-xmlrpc.conf.
ls /etc/apache2/conf-available/
block-xmlrpc.conf javascript-common.conf security.conf
charset.conf localized-error-pages.conf
ls /etc/apache2/conf-enabled/
block-xmlrpc.conf javascript-common.conf security.conf
charset.conf localized-error-pages.conf Step 2: Identify and edit the configuration file
sudo nano /etc/apache2/conf-available/block-xmlrpc.confStep 3: Add Jetpack IPs for whitelisting
this is how the default config file looks like:
<IfModule mod_rewrite.c>
<Directory / >
Redirect 301 /xmlrpc.php /
</Directory>
</IfModule>this is how the config should look like with the Jetpack IPs:
<IfModule mod_rewrite.c>
<Directory / >
RewriteEngine On
RewriteCond %{REQUEST_URI} ^/xmlrpc\.php$
RewriteCond %{REMOTE_ADDR} !^YOUR_DROPLET_IP$
RewriteCond %{REMOTE_ADDR} !^185\.64\.140\.
RewriteCond %{REMOTE_ADDR} !^192\.0\.78\.
RewriteCond %{REMOTE_ADDR} !^195\.234\.108\.
RewriteRule ^/xmlrpc\.php$ - [R=403,L]
</Directory>
</IfModule>Reference for Allowlisting Jetpack IPs:
Refer to the Jetpack support page for detailed instructions on adding Jetpack IPs to your allowlist.
Step 4: Enable the configuration and restart Apache2
sudo a2enconf block-xmlrpc.conf
sudo systemctl restart apache2Step 5: Verify and test your new configuration
To ensure that only the specified IP addresses can access xmlrpc.php, you can test access from different IPs or use a service that allows you to simulate requests from specific IP addresses.
Ensure xmlrpc.php is accessible to Jetpack by using curl.
curl -I https://yourwebsite.com/xmlrpc.phpConclusion
By following these steps, you can resolve the Jetpack reconnection error on a DigitalOcean WordPress droplet. This modification keeps your site secure while allowing essential Jetpack functionality.
Other useful articles that you might be interested in:
Troubleshooting WordPress 6.3.1: Common Issues and How to Fix Them
HTTP/2 WordPress Apache: How to Enable it on Your Site
Understanding and Protecting Against WordPress Vulnerabilities
What is fail2ban? The tools every Linux server admin must have